What is DAST, and How Can It Help You with Web Security?
In today’s world, it’s more important than ever to keep your data secure. In the past, companies only had to worry about the physical security of their buildings and belongings.
With increased reliance on technology in all aspects of our lives, businesses must also be concerned with digital security. This is where DAST comes into play.
Dynamic application security testing scans are a type of software that can help you identify vulnerabilities in your applications before cybercriminals exploit them for nefarious purposes like identity theft or fraud.
To learn more about how DAST works and what it entails, the different types, methodologies, and tools.
What Is DAST?
DAST, or dynamic application security testing, is a type of software that scans your applications for vulnerabilities before hackers find them.
It works by simulating real-world attacks against your applications to identify any potential weak points. It scans an entire application at once rather than targeting specific entry points like other methods such as manual testing or dynamic application analysis (DAA).
This differs from static application security testing (SAST), which relies on reviewing code rather than attacking the app.
Why And When To Use DAST?

There are a few key reasons why you might want to use DAST as part of your overall web security strategy:
To find and fix vulnerabilities before cybercriminals exploit themTo assess the risk of specific vulnerabilities and determine their priority for remediationTo evaluate the effectiveness of your current security controls
DAST is most useful when you want to test your entire app’s security in one fell swoop rather than targeting specific entry points.
It’s best to use DAST before any serious production problems occur because the sooner you find vulnerabilities in your apps, the easier they are to fix.
How Does DAST Work?
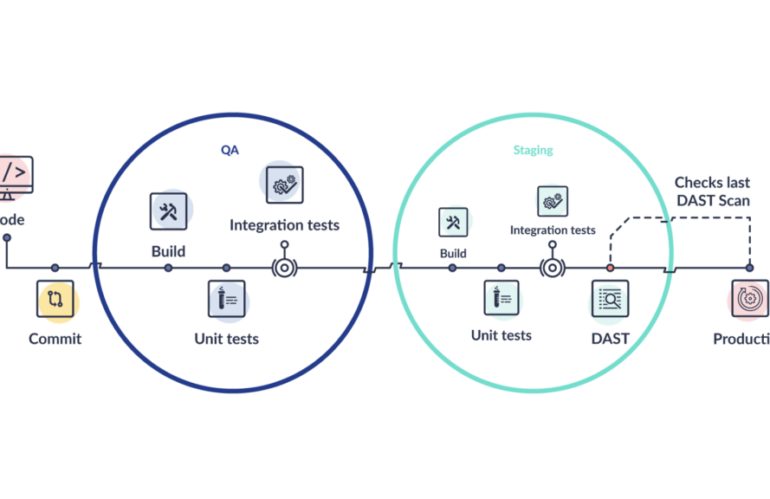
DAST scanning is a manual process requiring an expert to use specialised software, probing your web applications for vulnerabilities.
This is different from SAST testing, where the application’s source code needs to be modified before you can scan it.
DAST scans can take hours to days depending on how many requests and responses an app generates and network latency between a scanner and server hosting that application.
In general, though, most web applications with fewer than 100 pages will only take a few hours or less for scanning services to complete their analysis of each page/function within those pages.
This assumes no issues were found during testing – if security flaws are located, this process could last much longer due to the time needed for remediation work developers and QA testers.
Importance of DAST in application security?
DAST is an integral part of web application security testing for a few key reasons: first, it can help identify vulnerabilities in web applications that you may otherwise miss.
Additionally, DAST can test entire applications rather than specific entry points, making it a valuable tool for organisations with large and complex web presences.
Finally, DAST scanning is relatively quick and easy to set up compared to other forms of security testing – making it an excellent option for companies who want to improve their app’s security posture without dedicating too much time or resources.
In short, benefits of using DAST in application security include:
The ability to find vulnerabilities that you may miss with other testing methods.Focused scanning of entire applications, rather than just specific entry points.Quick and easy setup compared to other security testing options.
What Are The Different Types Of DAST?

When it comes to DAST, there are three primary types of scans: static, dynamic, and hybrid.
Static scanning is the process of evaluating source code for vulnerabilities. This scan looks at the code itself rather than how it functions when executed. While this method is less comprehensive than dynamic or hybrid scanning, it can still be effective in identifying specific types of issues – like buffer overflows and cross-site scripting (XSS) attacks.Dynamic scanning refers to evaluations that are performed while an application is running. This scan tests how the application behaves when accessed by a user and what happens behind the scenes when requests and responses are sent between the server and client machines. Dynamic scans are more comprehensive than static scans. Still, they can also be more challenging to execute and may require specific credentials to access certain application areas.Hybrid scanning is a combination of static and dynamic scans. This approach allows testers to understand better how an application functions by looking at both the code itself and how it behaves when executed. Hybrid scans are less likely to produce false positives than static or dynamic scanning alone.
What is DAST Automation?
DAST automation involves using scripts or bots to launch attacks against an application to identify vulnerabilities automatically.
You can use this approach alongside manual testing, allowing testers to focus on areas that may be more difficult to probe with automated tools.
Additionally, it helps reduce the time needed for a full scan by automating some of the tasks involved.
However, there are a few downsides to using DAST automation: not all vulnerabilities are discovered, and false positives can occur if tests are not correctly calibrated.
Despite these potential issues, using bots for security scanning is becoming increasingly popular due to the sheer number of applications present on the web today – it would simply be impossible for humans alone to test all of them manually.
What Are The Different Methodologies And Tools For DAST?

There are several different types of DAST tools on the market today, each with its unique capabilities. Some focus more on finding vulnerabilities, while others help automate certain aspects of scanning so that you don’t have to do as much manual work.
Regardless, there are some key features all great web application scanners should have:
The ability to scan both static and dynamic content.A wide range of scanning options, such as targeting specific areas of an application or testing for particular vulnerabilities.The ability to scale to meet the needs of large organisations.Automated testing capabilities can help reduce the time needed for a full scan.
The two primary methodologies used when evaluating DAST tools are the white box and the black box.
White-box techniques give testers full knowledge of their environment by providing them with passwords needed for scanning and other relevant data like API keys or user names/passwords associated with specific actions in certain apps or functions within those apps.
Black-box methods occur under more stringent conditions where testers don’t know much about your environment, i.e., they are not given access credentials.
For example, a black-box tester might only be given the URL of an application and expected to find vulnerabilities without further instructions or information.
Of course, there are a few different tools that fall under these methodologies as well:
White Box
Veracode GreenlightFortify On DemandIBM AppScan DAST Toolkit
Black Box
Netsparker Application Security Scanner (Tenable Network Security),Acunetix Web Vulnerability Scanner,HPE SiteScope with Twistlock Security Center plugin for capturing web requests and responses.
How To Conduct DAST?
DAST can be used by all types of organisations, including those with a small number of applications and others that manage hundreds or even thousands.
It is recommended that you start using DAST in tandem with manual testing since it doesn’t always cover all the bases.
Once you become more familiar with web application security scanning and how your tool works, however, there are some steps you should take to ensure optimal results:
Start by manually verifying any functions on an application’s front-end and back-end for vulnerabilities. This will help identify issues before running automated tests, so they don’t waste time going over areas already verified as safe from attack.Run scans at least once a quarter but aim for monthly. The more often you run scans, the better. This will help keep your applications up-to-date with new vulnerabilities and make sure any previously discovered ones are fixed as well.Target specific areas within an application rather than testing for all possible security issues at once (looking only at specific pages or functions may result in a false sense of security).
If you conduct DAST manually, be aware that there is no single best methodology to use across every organisation’s web apps.
You’ll have to pick one method now but can easily switch it up later if needed depending on what works best for your current needs.
Strengths and Weaknesses of DAST
Strengths
It is an inexpensive way to find many of the vulnerabilities in your web applications, including those that are new or not easily identified by manual testing.
Since DAST tools can run continuously and automatically, they will help ensure no new issues pop up after you’ve fixed prior ones.
Weaknesses
Though useful for smaller organisations with just a handful of apps under control, it may be challenging to scale DAST across large environments without some automation (like API scanning).
Furthermore, because automated scanners don’t provide as much detail on what exactly might be wrong at any given time as manual testers would do during white-box testing procedures, more detailed reporting may also prove challenging when trying to address specific security.
Top 4 DAST Tools You Can Use

There are many DAST tools on the market these days, and picking the right one for your organisation can be overwhelming. Listed below are four popular scanners with a brief description of each to help you get started:
Astra Vulnerability Scanner
Astra vulnerability scanner is designed to discover and verify vulnerabilities and exploit them in applications and networks.
With the Astra Pentest DAST tool, you’ll be able to find SQL Injection, Cross-Site Scripting/XSS, Remote File Inclusion, Directory Traversal & SSRF issues, along with many other types of vulnerabilities.
It also comes complete with an easy-to-use dashboard so novice testers won’t have any trouble using it right away, even if they’ve never performed a pen test before.
Veracode Greenlight
Best suited for cloud-based applications, Veracode Greenlight is designed to identify vulnerabilities in both web and mobile apps quickly. It offers an easy-to-use interface and detailed reports that include remediation advice.
Fortify On Demand
This tool provides comprehensive security scanning for both web and mobile applications. In addition to identifying vulnerabilities, it also rates their severity so you can focus on the most important ones first.
Fortify also has a web interface that makes it easy to start scans no matter what browser you’re using.
Acunetix
Acunetix is a web vulnerability scanner that scans for SQL Injection, Cross-Site Scripting/XSS, Local File Include & Remote File Include vulnerabilities.
It also features an easy to use dashboard with detailed reports you can generate based on the data it provides during testing procedures.
Acunetix has both desktop and cloud versions available, so you’ll be able to take advantage of its powerful scanning technology no matter where your applications are hosted or how large they may be.
Conclusion
DAST is an integral part of application security and should be used alongside SAST to get a more holistic view of your app’s vulnerabilities.
There are many different DAST tools and methodologies, each with its strengths and weaknesses.
DAST scans can take anywhere from hours to days, depending on the size and complexity of the application being tested – but it’s worth noting that you can scan most web applications in a relatively short amount of time frame.
Additionally, DAST automation can help speed up the scanning process while still providing valuable results.
As always, make sure to consult with your development team before implementing any new security measures into your apps!
The post What is DAST, and How Can It Help You with Web Security? is by Stuart and appeared first on Inkbot Design.
Read more: inkbotdesign.com